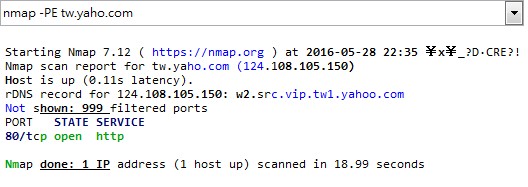
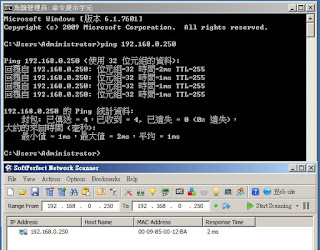
afp-serverinfo.nse說明
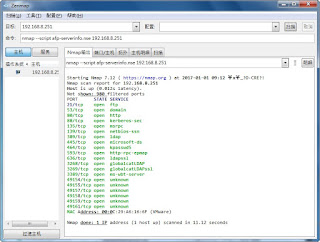
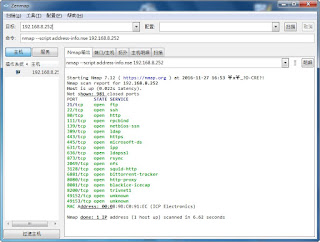
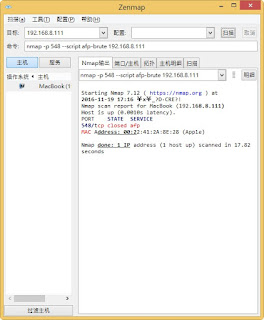
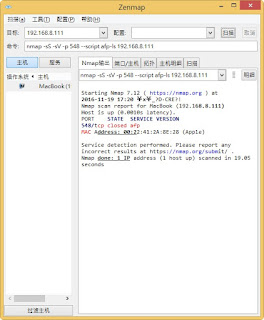
查詢伺服器 一些訊息 指令: nmap --script afp-serverinfo.nse 192.168.8.251 官方說明: https://nmap.org/nsedoc/scripts/afp-serverinfo.html 內容: local afp = require "afp" local nmap = require "nmap" local shortport = require "shortport" local stdnse = require "stdnse" local table = require "table" description = [[ Shows AFP server information. This information includes the server's hostname, IPv4 and IPv6 addresses, and hardware type (for example <code>Macmini</code> or <code>MacBookPro</code>). ]] --- -- @output -- PORT STATE SERVICE -- 548/tcp open afp -- | afp-serverinfo: -- | Server Flags: -- | Flags hex: 0x837d -- | Super Client: true -- | UUIDs: false -- | UTF8 Server Name: true -- | Open Directory: true -- | Reconnect: false -- | Server Notifications: true -- | TCP/IP: true -- | Server Signature: true -- | Server Messages: true -- | P