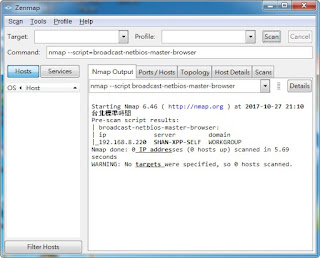
broadcast-pc-anywhere 說明
這是 用來找LAN 裡頭 可有pcanywhere 軟體client 指令: nmap --script broadcast-pc-anywhere 官方網址: h ttps://nmap.org/nsedoc/scripts/broadcast-pc-anywhere.html 內文: local nmap = require "nmap" local os = require "os" local stdnse = require "stdnse" local table = require "table" description = [[ Sends a special broadcast probe to discover PC-Anywhere hosts running on a LAN. ]] --- -- @usage -- nmap --script broadcast-pc-anywhere -- -- @output -- Pre-scan script results: -- | broadcast-pc-anywhere: -- |_ 10.0.200.113 - WIN2K3SRV-1 -- -- @args broadcast-pc-anywhere.timeout specifies the amount of seconds to sniff -- the network interface. (default varies according to timing. -T3 = 5s) author = "Patrik Karlsson" license = "Same as Nmap--See http://nmap.org/book/man-legal.html" categories = { "broadcast", "safe" } local TIMEOUT = stdnse.parse_timespec(stdnse.get_script_args("broadcast