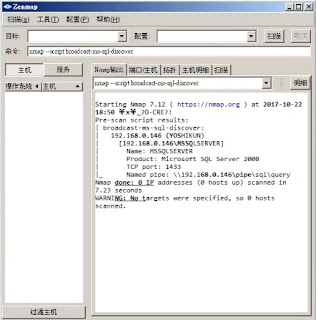
broadcast-netbios-master-browser說明
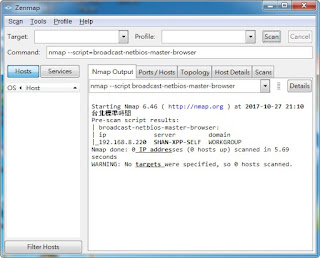
尋找LAN 有使用 netbios 通訊協定 的電腦..... nmap --script=broadcast-netbios-master-browser 官方說明: https://nmap.org/nsedoc/scripts/broadcast-netbios-master-browser.html 內文: local bit = require "bit" local netbios = require "netbios" local nmap = require "nmap" local stdnse = require "stdnse" local tab = require "tab" description = [[ Attempts to discover master browsers and the domains they manage. ]] --- -- @usage -- nmap --script=broadcast-netbios-master-browser -- -- @output -- | broadcast-netbios-master-browser: -- | ip server domain -- |_10.0.200.156 WIN2K3-EPI-1 WORKGROUP -- -- Version 0.1 -- Created 06/14/2011 - v0.1 - created by Patrik Karlsson <patrik@cqure.net> author = "Patrik Karlsson" license = "Same as Nmap--See http://nmap.org/book/man-legal.html" categories = {"broadcast", "safe"} prerule = function() return true end local functio