broadcast-dropbox-listener.nse 說明
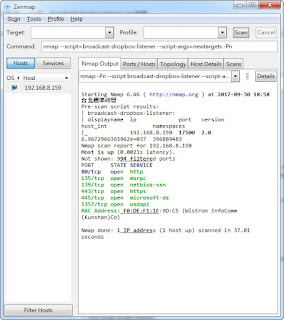
針對內網, 檢查broadcast 是否有發送dropbox封包 當然... 防毒防火牆軟體 可以阻擋 此類型封包 官方說明: https://nmap.org/nsedoc/scripts/broadcast-dropbox-listener.html 內文: local json = require "json" local nmap = require "nmap" local stdnse = require "stdnse" local tab = require "tab" local target = require "target" description = [[ Listens for the LAN sync information broadcasts that the Dropbox.com client broadcasts every 20 seconds, then prints all the discovered client IP addresses, port numbers, version numbers, display names, and more. If the <code>newtargets</code> script argument is given, all discovered Dropbox clients will be added to the Nmap target list rather than just listed in the output. ]] --- -- @usage -- nmap --script=broadcast-dropbox-listener -- nmap --script=broadcast-dropbox-listener --script-args=newtargets -Pn -- @output -- Pre-scan script results: -- | broadcast-dropbox-listener: -- | displayname ip